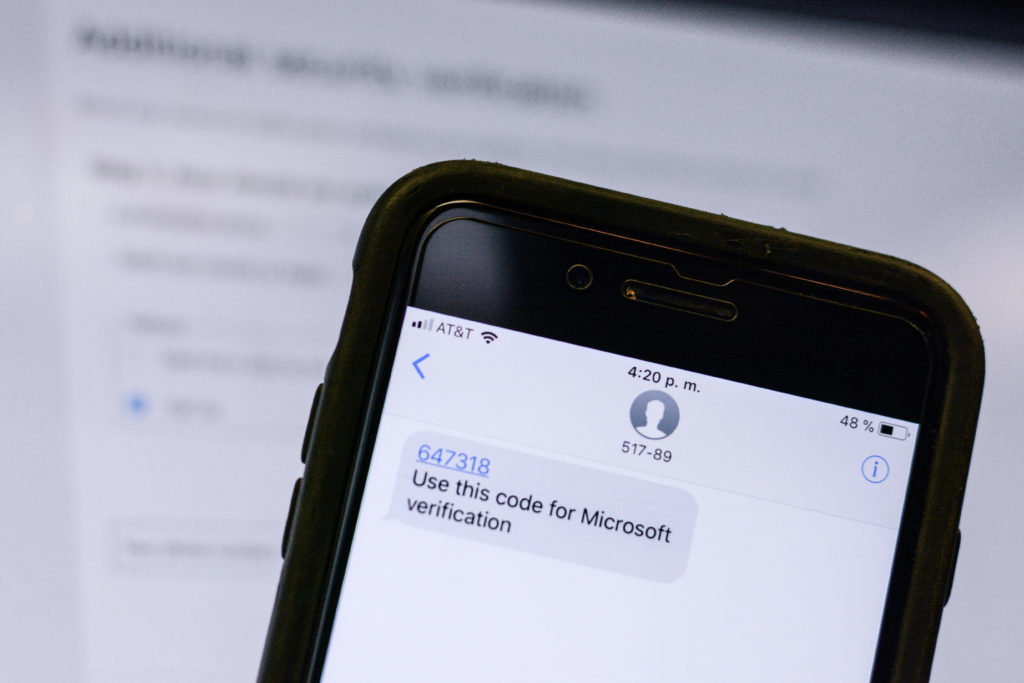
The University is implementing a new security measure designed to guard against cyberattacks on students, faculty and staff.
Officials are starting a two-step authentication process that will require users to enter a code sent to their phone or tablet for access to their GW email accounts beginning Jan. 30. Cybersecurity experts said the move will increase protection of private information, a difficult task because large university networks are particularly vulnerable to cyber criminals.
Officials said in an email last week that the new feature for student accounts will start in January, rather than this month as was initially announced, to space out the transition process. Students who sign up early for two-step authentication online are eligible for a $25 GWorld credit, according to the Division of Information Technology website.
Faculty and staff in the Graduate School of Education and Human Development started to implement the new security measure Tuesday, the first of many schools to participate in a phased transition of faculty email accounts, according to the website.
Chief Information Officer Loretta Early said officials decided to implement the new measure after hackers used phishing scams – emails that appear to be legitimate but are actually attempts by hackers to gain access to private information – to target university accounts.
In 2016, the IT division invested in technical controls and education to better protect students against phishing scams.
Early said students, faculty and staff are targeted by scammers everyday, but the number of attacks has stayed relatively consistent in recent years. She said phishing scams are hard to detect and two-step authentication won’t ensure students are fully protected, but it is a proactive and “reasonable” measure that provides an additional layer of security.
“We wanted to make sure we were giving the GW community the best tools to protect their accounts and their data, and we think two-step authentication does that job very well,” Early said in an email.
To mark National Cyber Security Awareness month in October, the IT division hosted several events about password strength and cybersecurity. This week, GW Libraries will host Privacy Week, a series of events designed to teach students about security and privacy in the digital age.
Early said the transition to two-step authentication was postponed until January because the process requires accounts who receive the added feature to be stored at an external server.
“The overnight process to establish the group for faculty and staff was taking too long to complete the night before,” she said. “We decided to postpone the switch and change the approach to go live with smaller groups at a time, and we will be using the same approach for students.”
Danielle Zeedick, a professor of cybersecurity, said this kind of security measure is necessary because passwords are not strong enough to keep information protected and can easily be hacked.
She said switching to two-step authentication should not be a huge adjustment for students because many already use it for other online commercial services.
“I don’t think it should be seen as an inconvenience,” she said. “It’s like online banking or online shopping, just to ensure you are who you say you are.”
There many different kinds of identifying information – like social security numbers – that hackers can use to commit identity theft that can be found on a university account, she said.
Jean-Pierre Auffret, the associate director of the Center for Assurance Research and Engineering at George Mason University, said universities in particular are at risk to hackers because their networks are large, relatively unsecured and contain vulnerable information like intellectual property and health care information.
There are thousands of students and a large number of faculty who have access to these systems, he said. Universities also partner with corporations and other institutions for activities like research, which opens up their networks to more risk.
“By nature of a university’s role and work, they are fairly open,” Auffret said. “It’s quite an open environment.”
He added that even raising awareness of security risk by announcing a new authentication process could help students and faculty protect their accounts. GW is not the first to add this security measure, but he said it is not behind the trend.
Almost all of GW’s 18 peer universities, except for American University, has two-step or multi-factor authentication for email accounts.
“Because they are such large targets, more and more universities are moving toward two-step authentication,” Auffret said.